Everything you need to build a trusted, future-proof, and robust solution

End-to-end security management is essential to safeguard integrity, to ensure trusted connections, to protect systems against cyber attacks, and to protect data privacy among others.
IoT is opening new business opportunities across nearly every sector, but when we multiply the connections between the physical world and the cyber world, we also multiply the risks.
We, therefore, need to:
- safeguard integrity of code running on devices.
- authenticate users and their devices.
- protect your system from cyber and physical attacks.
- protect the privacy of sensitive user data.
MobileKnowledge will help you choose the right end-to-end security measures tailored to your solution, at device, network and system levels, and in the most effective and efficient way.
Security needs to be built in from the start, with device and data security fully integrated to protect all IoT applications and solutions
A complete understanding of the application allows the user to identify possible threats and, therefore, decide on the security measures to incorporate.
Whether you want:
- to protect your brand and ensure the authenticity of each of the devices within the network.
- to ensure you have a secure and trusted connection to the backend.
- to protect the end consumer’s data privacy.
- or to protect your system software from attackers by ensuring a secure boot and secure update.
Maintain full control of your solution when deployed in the field and avoid attackers damaging your business.
We will help you build a holistic security approach to your solution
Our services cover the complete IoT ecosystem, from hardware and embedded firmware-related services to mobile or cloud connection gateway solutions up to cloud services development or integration with existing platforms.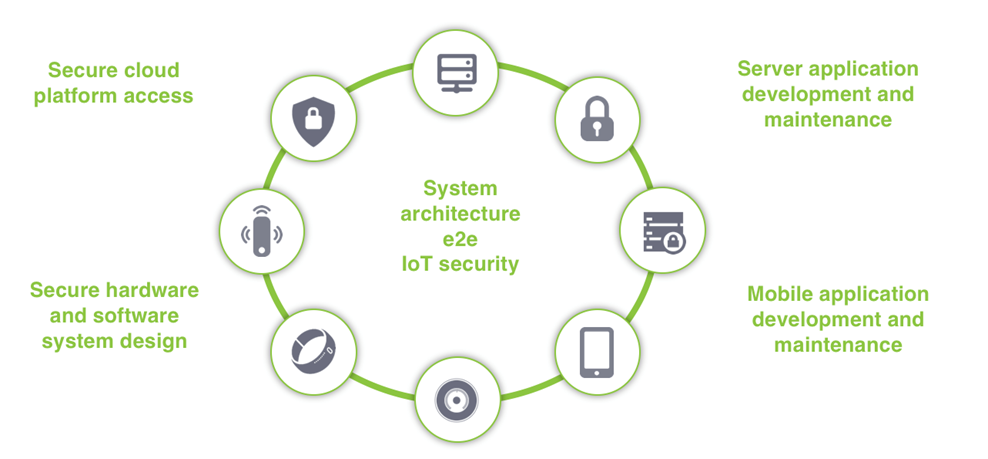
MobileKnowledge services in e2e IoT applications
We are your ideal engineering consultant for any specific support in connection with your IoT developments, applications and related secure ecosystem.
We design and develop secure HW systems, embedded FW, mobile phone and secure cloud applications.
For more information, you can download the presentation here.
